In today’s mobile-first world, it’s easy to download apps without thinking twice. But some of those convenient tools could be doing more than helping you track your fitness goals or check the weather—they could be spying on you. Did you know that over 70% of mobile apps collect more data than they need to function?” According to research by NordVPN, 87% of Android apps and 60% of iOS apps request access to device functions unrelated to their performance—often including your location, camera, microphone, and more.
As a leading Managed Service Provider (MSP) in the Lehigh Valley, EZ Micro helps small and medium-sized businesses protect their employees and data from hidden security risks, including risky phone apps. Here’s what you need to know and how our team can help.
The Hidden Threat of Malicious Mobile Apps
Many free apps, especially those found outside of official app stores or from unknown developers, contain hidden tracking tools or malware. These apps can:
- Access your microphone and camera without permission prompts
- Track your location 24/7—even when the app isn’t open
- Collect sensitive business information like contacts, emails, and files
- Send data to third parties, including advertising networks and potentially malicious actors
In some cases, these apps are part of more complex phishing or spyware campaigns designed to breach your business’s network through mobile endpoints.
Red Flags to Watch For
Not all suspicious apps are obvious. Here are a few warning signs:
- Apps that ask for unnecessary permissions (e.g., a calculator asking for microphone access)
- Apps not available in the Apple App Store or Google Play Store
- Poor user reviews and limited developer information
- Sudden battery drain or data usage spikes
How to Protect Your Devices and Your Business
If you’re concerned about privacy and data security, especially on mobile devices, there are several best practices you can implement right away—no IT team required.
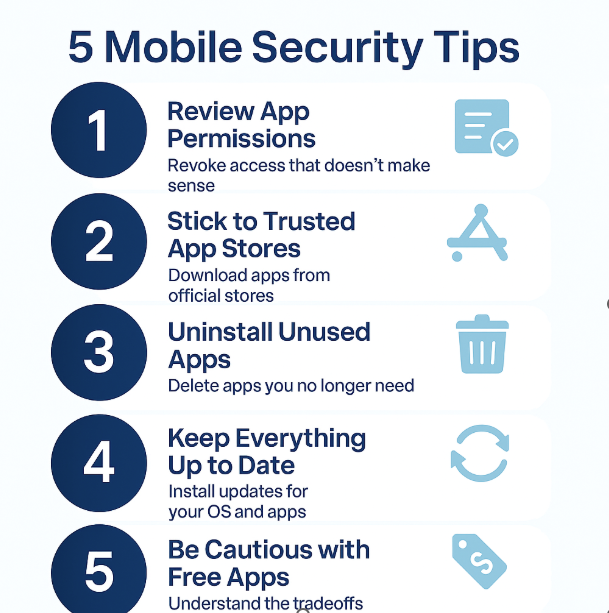
1. Review App Permissions
Go through the settings on your phone and look at which apps have access to your microphone, camera, location, contacts, and more. Revoke anything that doesn’t make sense. For example, a flashlight app doesn’t need access to your microphone.
2. Stick to Trusted App Stores
Only download apps from the Apple App Store or Google Play Store, and double-check reviews, ratings, and the developer’s credibility before installing anything new.
3. Uninstall Unused Apps
If you’re not using an app regularly, it’s safer to delete it. Some dormant apps may continue collecting data in the background.
4. Keep Everything Up to Date
Install software updates for both your phone’s operating system and your apps as soon as they’re available. These often contain patches for newly discovered security vulnerabilities.
5. Be Cautious with Free Apps
Free apps are often supported by advertising, which means your data might be collected and sold. Always consider the tradeoff between convenience and privacy.
Stay Informed and Stay Secure
At EZ Micro, we encourage all businesses to take mobile and personal cybersecurity seriously—even when it falls outside of traditional IT support. While we don’t manage personal phone security or apps, we’re big believers in cybersecurity awareness and proactive protection at every level of your business.
EZ Micro’s Role in Protecting Your Business
As a full-service Managed IT Provider for businesses in the Lehigh Valley, EZ Micro offers:
- Proactive IT Support
We monitor and maintain your systems 24/7 to catch and resolve issues before they impact your business.
- Cybersecurity Protection
We implement layered security measures like endpoint protection, email filtering, firewalls, and more to keep your business safe from threats.
- Strategic Technology Planning
We help you plan for future upgrades, compliance needs, and business growth.
- Cloud Solutions & Data Backup
We manage cloud environments, ensure secure data storage, and provide disaster recovery solutions to minimize downtime.
- Compliance & Risk Mitigation
We help ensure your technology meets industry standards for HIPAA, PCI, and cyber insurance requirements—reducing your exposure to fines and breaches.
Whether you’re in manufacturing, legal, healthcare, or nonprofit work, your team relies on mobile devices every day. Don’t let a simple download become a serious data breach. Contact us today!